Welcome to Tyrian Risk, Inc.
Our mission is to ACHIEVE
Zero Trust Data Security
through DATA DRIVEN strategies
Tyrian Risk, Inc was founded on these core principles:
- Red team tactics should inform Blue team priorities;
- Effective risk management requires accurate risk metrics;
- Attackers think in graphs, and Defenders think in lists.
Better defense can be achieved by leveraging Graph technologies. Hence, our solutions are built using the latest Graph Neural Network Machine Learning breakthroughs from Drug Discovery research labs.
New cybersecurity incident reporting regulations, require disclosure within as soon as 72 hours make our boutique range of cyber resilience and response services more important than ever:
- RECOVER faster from critical RANSOMWARE outages
- FIND hostile agents lurking on your network with Threat Hunts
- COMPLY with cybersecurity incident reporting regulations
- ACHIEVE Zero Trust Data Security with our full stack solutions
Services
Our expert team specializes in incident response and digital forensics, ready to tackle ransomware, data breaches, cyber security incident reporting regulatory compliance and more. Swift and effective incident response is our forte, ensuring minimal impact and rapid recovery. With cutting-edge forensic capabilities, we uncover the root cause of attacks, enabling you to strengthen defenses and prevent future incidents. Trust us to navigate the complex cyber threat landscape, providing proactive defense strategies and empowering your team with the tools and knowledge needed to safeguard your business. Leverage our incident response and DFIR services, to enhance your cyber resilience, reduces risks associated with Malware, phishing and ransomware, and accelerate your journey to a Zero Trust!
- FIND hostile agents lurking on your network with Threat Hunts
- COMPLY with cyber security incident reporting regulations
- PROTECT against insider threats with our digital forensics
- CONTAIN incidents in progress with our incident response
- SECURE your Cloud systems with Automation Orchestration and Response
- COUNTER adversary tactics with Mitre ATT&CK Risk Metrics
- VERIFY and monitor every access request; Achieve Zero Trust Data Security
- EXPERT cybersecurity guidance & risk management with a Virtual CISO
Threat Hunting

Our Forensic Deep Scan Threat hunting services take a proactive cybersecurity approach that involves actively searching for signs of malicious activities or security breaches within an organization's network. Unlike traditional cybersecurity measures that focus on reactive responses to known threats, threat hunting is about actively seeking out potential threats before you become a victim of cybercrime.
By continuously monitoring networks and endpoints to detect and mitigate potential threats, and by leveraging threat intelligence and advanced analytics, threat hunting teams can uncover ransomware, malware, and phishing attempts before they cause significant damage. Through targeted searches and analysis, threat hunters can identify indicators of compromise, anomalous behavior, and suspicious patterns indicative of ransomware attacks, malware infections, and phishing campaigns.
Our Threat Hunters, use our proprietary tools, techniques, and expertise to identify anomalies, suspicious patterns, and indicators of compromise that may indicate the presence of a malicious cyber actors (MCAs). This process involves analyzing large volumes of data, typically 100's of Gb, including network traffic logs, endpoint data (EDR) and SIEM, and investigating system behavior, to uncover hidden threats that may have evaded traditional security measures.
By continuously monitoring and investigating your network infrastructure for potential threats, we enable organizations to proactively detect and disrupt the initial footholds established by MCA's before they escalate into full-blown breaches. Our proactive Threat Hunting ensures organizations stay ahead of cyber adversaries, enhance their overall security posture, and minimize the impact of potential cyber attacks, like ransomware, phishing and malware.
Cyber Incident Response

In today's digital landscape, the threat of cyber incidents looms large, posing significant risks to businesses of all sizes. We understand the critical importance of swift and effective cyber incident response. Our dedicated team of experts is here to provide unparalleled support and guidance in the event of a cyber attack or security breach. With our comprehensive cyber incident response services, we offer round-the-clock monitoring, rapid detection, and immediate response to contain and mitigate the impact of any security incident, and cybercrime.
Our Cyber Incident Response Team offers unparalleled services in combating phishing, malware, and ransomware threats, ensuring your organization's resilience against cyber attacks. With expertise in threat detection, containment, and eradication, our team swiftly responds to security incidents, minimizing damage and restoring operations efficiently and ensuring data security. By partnering with us, you can rest assured that your organization is equipped with the latest tools and strategies to combat cyber threats effectively. Our tailored incident response plans are designed to minimize downtime, protect sensitive data, and safeguard your reputation in the face of adversity. Don't wait until it's too late. Take proactive steps to secure your digital assets and ensure business continuity with our top-tier cyber incident response services. Trust us to be your reliable partner in navigating the complex and ever-evolving cybersecurity landscape.
Digital Forensic Investigations

Threats don't always come from the outside, discretion and impartiality is vital when handling insider investigations. Our digital forensic investigations involve the systematic collection, preservation, analysis, and presentation of digital evidence to uncover facts related to cyber incidents, crimes, or disputes. Our digital forensics experts use specialized tools and techniques to examine electronic devices, such as computers, smartphones, servers, storage media, social media, and cloud data to extract and interpret data that can be used as evidence in legal proceedings. We follow a strict methodology to ensure the integrity and admissibility of the evidence collected, including identifying and securing the digital evidence, creating forensic images of storage devices, conducting in-depth analysis of data, and documenting findings in a detailed report. Our DFIR experts conduct in-depth forensic analysis to identify the root cause, damage, and attribution of cyber incidents.
We have experience conducting digital forensic investigations in a variety of scenarios, including cybercrime, data breaches, intellectual property theft, employee misconduct, civil litigation, and divorce proceedings. We assist clients in all these scenarios, helping to uncover new digital evidence, to reconstruct events, identify perpetrators, establish timelines, and support legal proceedings with credible evidence. Our professionals work as a trusted third party to ensure evidence is extracted and collected correctly preserving the chain of custody to ensure that you achieve a successful outcome.
Big Data Fraud Analytics

Big data analytics is a game-changer in fraud prevention, leveraging advanced statistical analysis techniques to detect and investigate fraudulent activities effectively. We use big data analytics to revolutionize fraud prevention, providing organizations with the tools and insights needed to detect, investigate, and prevent fraudulent activities effectively. By leveraging advanced statistical analysis techniques and big data technologies, we help them stay ahead of fraudsters, protect their assets, and safeguard against financial losses and reputational damage associated with fraud.
Key capabilities we bring to the table include:- Data Aggregation and analysis of vast amounts of structured and unstructured data from diverse sources, including transaction logs, customer records, external feeds, to provide a holistic view of potential fraud patterns and anomalies.
- Pattern Recognition utilizing sophisticated algorithms and machine learning models to identify complex fraud patterns and detect anomalies that may indicate fraudulent behavior. By analyzing historical data and real-time transactions, organizations can uncover irregularities and flag suspicious activities for further investigation.
- Predictive Modeling to forecast potential fraud risks based on historical trends and patterns,enabling identification of emerging fraud schemes, anticipating fraudulent activities, and take preventive measures to mitigate risks.
- Real-time Monitoring of data streams, allows organizations to detect fraudulent activities as they occur. By applying advanced analytics in real-time, organizations can respond promptly to suspicious transactions, reduce false positives, and prevent financial losses associated with fraud.
- Automation and Efficiency of fraud detection processes, streamlines investigations, and enhances the efficiency of fraud prevention efforts. By leveraging machine learning algorithms, we help organizations scale their fraud detection capabilities, improve accuracy, and reduce manual intervention in fraud investigations.
Cloud Security Orchestration, Automation and Response
Our services integrate various security tools, technologies, and processes within cloud environments, to streamline security operations, enhance visibility, and improve incident response capabilities. Security orchestration in cloud environments involves the automation and coordination of security processes and controls to effectively manage and respond to security incidents and threats. Orchestration plays a crucial role in ensuring the consistent enforcement of security policies, compliance requirements, and best practices across dynamic and distributed cloud infrastructures. By orchestrating security tasks such as threat detection, incident response, vulnerability management, and access control, organizations can effectively mitigate risks and protect their cloud assets from cyber threats.
We implement SOAR solutions for the following providers:
- Microsoft 365 (M365) Cloud Email: Our cutting-edge cybersecurity services for cloud email, tailored specifically for Microsoft Office and M365 environments, offer a comprehensive approach to safeguarding your organization's data integrity and confidentiality. Leveraging key Microsoft technologies such as Purview, Data Governance, Defender, and Entra, we provide advanced solutions to enhance data security within your cloud email ecosystem. Microsoft Purview enables comprehensive data governance and compliance by providing a unified view of your data landscape, facilitating effective data classification and protection strategies. Data Governance in M365 ensures data security and compliance through policy enforcement, access controls, and data loss prevention measures. Microsoft Defender offers robust endpoint protection, threat detection, and response capabilities to defend against evolving cyber threats targeting cloud email platforms. Entra enhances identity and access management, enabling secure authentication and authorization protocols to prevent unauthorized access to sensitive data. By integrating these key Microsoft technologies into our cybersecurity services, we empower organizations to proactively manage data security risks, detect and respond to threats effectively, and maintain regulatory compliance in their cloud email environments. Trust us to strengthen your data security posture, mitigate risks related to malware, phishing and ransomware, and safeguard your critical information assets with confidence.
- AWS (Amazon Web Services) prioritizes cloud security by offering a comprehensive suite of services to protect data and applications hosted on its platform. In addition to robust identity and access management through AWS IAM, AWS provides advanced logging and monitoring capabilities. AWS CloudTrail enables logging and monitoring of API calls, providing visibility into user activity and resource changes for security analysis and compliance auditing. AWS Config allows for continuous monitoring and assessment of AWS resource configurations to ensure compliance with security best practices. Moreover, AWS offers incident response capabilities through services like AWS Security Hub and Amazon GuardDuty. These services provide threat detection, automated alerts, and actionable insights to help you respond swiftly to security incidents. Leveraging AWS's logging and incident response tools, we enhance your security posture, detect and respond to threats effectively, and maintain a secure cloud environment.
- Microsoft's Azure: offers a wide array of tools and services to protect cloud workloads. Azure Active Directory (AD) provides secure identity management, access control, and single sign-on capabilities. Azure Security Center offers advanced threat detection and security monitoring, including logging and analysis of security events to identify potential threats.Azure also provides robust incident response capabilities through Azure Monitor and Azure Sentinel. Azure Monitor enables logging, monitoring, and alerting on Azure resources and applications, while Azure Sentinel offers cloud-native security information and event management (SIEM) for advanced threat detection and response. By leveraging Azure's logging and incident response tools, organizations can proactively monitor their cloud environments, detect security incidents in real-time, and respond effectively to mitigate risks and protect their assets.Additionally, Microsoft Defender for Endpoint (formerly Microsoft Defender Advanced Threat Protection) offers endpoint detection and response (EDR) capabilities to protect devices across the organization. By leveraging machine learning and behavioral analytics, Defender for Endpoint detects and responds to advanced threats on endpoints, helping organizations prevent, detect, investigate, and respond to security incidents effectively. Together, Microsoft Sentinel and Defender EDR provide a comprehensive security solution that strengthens Azure's security posture and helps organizations defend against evolving cyber threats.

Key benefits of security orchestration in cloud environments include improved operational efficiency, faster incident response times, enhanced threat detection capabilities, and better overall security posture. By automating repetitive tasks, orchestrating security workflows, and integrating security tools seamlessly, organizations can strengthen their cloud security defenses and adapt to the evolving threat landscape effectively. Security orchestration in the cloud is essential for organizations looking to secure their cloud environments proactively and efficiently.
Mitre ATT&CK metrics

MITRE ATT&CK is a globally recognized framework that provides a comprehensive and structured model for understanding and categorizing cyber threats based on real-world adversary behaviors. ATT&CK serves as a knowledge base of tactics, techniques, and procedures (TTPs) used by threat actors during various stages of the cyber kill chain. ATT&CK is organized into matrices that categorize adversary behaviors across different platforms, including Windows, macOS, Linux, cloud environments, and mobile devices. Each matrix outlines tactics (high-level objectives) and techniques (specific methods) used by adversaries to achieve their goals, such as initial access, execution, persistence, privilege escalation, defense evasion, and exfiltration.
By mapping observed behaviors to the ATT&CK framework, we help organizations identify gaps in their defenses, prioritize security controls, and improve detection and response capabilities against known adversary tactics. Mitre Att&ck is a key layer in our solutions package, and is a key benchmark we use to measure performance and effectiveness of Security Operations Center (SOC) teams, to standardize threat intelligence sharing, conduct red team exercises, develop defensive strategies, create effective risk metrics. This lowers your risk exposure to cybercrime, ransomware, phishing and malware attacks.
Our Key Performance Indicators (KPIs) to measure security operations teams include:
- Detection Coverage: Measure the percentage of ATT&CK techniques covered by detection capabilities to assess the SOC's ability to identify known adversary behaviors.
- Mean Time to Detect (MTTD): Track the average time taken to detect security incidents mapped to ATT&CK techniques, indicating the efficiency of threat detection processes.
- Mean Time to Respond (MTTR): Monitor the average time taken to respond to and mitigate security incidents associated with ATT&CK tactics, reflecting the effectiveness of incident response efforts.
- Incident Response Time: Measure the time taken to investigate and respond to security incidents aligned with ATT&CK, ensuring timely incident resolution and containment.
- False Positive Rate: Evaluate the rate of false positives generated by security alerts mapped to ATT&CK techniques, aiming to reduce noise and improve alert accuracy.
- Adversary Tactic Coverage: Assess the percentage of ATT&CK tactics observed in security incidents, indicating the breadth of coverage in detecting adversary behaviors.
- Threat Hunting Effectiveness: Evaluate the number of successful threat hunting engagements targeting specific ATT&CK techniques, demonstrating the SOC's proactive detection capabilities.
- Adversary Simulation Results: Measure the success rate of red team exercises or penetration tests emulating ATT&CK tactics, providing insights into the organization's resilience against simulated attacks.
- Incident Containment Rate: Track the percentage of security incidents contained before further escalation, reflecting the SOC's ability to prevent threats from spreading across the network.
- Security Posture Improvement: Assess the number of security controls, processes, or technologies enhanced based on ATT&CK insights, demonstrating continuous improvement in security defenses.
By aligning SOC KPIs with the MITRE ATT&CK framework, organizations can effectively measure the performance of their security operations, enhance threat detection and response capabilities, and strengthen overall cybersecurity resilience against evolving cyber threats.
Zero Trust Data Security

Our consultants can help you achieve compliance with Zero Trust Architecture, with a particular focus on the Data Pillar. We can help you to prepare a comprehensive data management strategy as part of the zero trust approach. Our solutions will ensure you comply with National Institute of Standards and Technology (NIST) Special Publication (SP) 800-53, Rev 5 and (NIST) Special Publication (SP) 800-171 as required.
Key steps in the journey include:
- Identifying sensitive data and critical applications for introducing zero trust, and build a Data Catalog
- Develop an Enterprise Data Governance framework including policies, procedures, guidelines, processes and standards
- Deploy Data Labeling and Tagging to data; including automated discovery, classification and data analysis tools
- Identify users (including system & application accounts) to enable Data Access Monitoring across File, email, Sharepoint, Teams, IM, Slack, Database, DAAS and cloud Access
- Deploy data protection controls from Data Encryption & Rights Management, to Data Loss Prevention (DLP) and Database Activity Monitoring (DAM) and monitor data flows
- Robust Data Access Controls Multi-factor authentication, Break-glass system accounts and privileged user monitoring
- Apply least privilege or "need to know" authorization controls
Cyber Security Incident Regulations

We help companies comply with cyber security disclosure rules:
- SEC Cyber Security Disclosure of Material Incidents rule
- Cyber Incident Reporting for Critical Infrastructure Act
- Cybersecurity Maturity Model Certification Program 2.0
- New York DFS cybersecurity regulations, 23 NYCRR 500
72 Hours to report?
SEC Cyber Security rule
The Securities and Exchange Commission (SEC) has recently introduced new regulations aimed at enhancing cybersecurity incident reporting and disclosure requirements for public companies. These regulations mandate that companies disclose material cybersecurity incidents promptly to investors, shareholders, and the public to ensure transparency and accountability. Security Incident Disclosure required within 4 days via form 8-K
Under the new SEC regulations, public companies are required to disclose cybersecurity incidents that could have a significant impact on their operations, financial condition, or reputation. This includes incidents such as data breaches, ransomware attacks, unauthorized access to sensitive information, and other cybersecurity events that may pose a risk to the company and its stakeholders. The SEC's updated guidance published May 21, 2024 is here
Furthermore, the SEC regulations emphasize the importance of implementing robust cybersecurity policies, procedures, and controls to prevent, detect, and respond to cyber threats effectively. Companies are encouraged to conduct regular risk assessments, cybersecurity training, and incident response drills to strengthen their cybersecurity posture and mitigate the impact of potential incidents like ransomware, malware phishing and other cybercrime.
By enforcing stricter cybersecurity disclosure requirements, the SEC aims to improve transparency, accountability, and investor confidence in the face of increasing cyber threats and data breaches. Public companies are urged to prioritize cybersecurity preparedness and compliance with the new SEC regulations to safeguard their operations and protect shareholder interests.
Cyber Incident Reporting for Critical Infrastructure Act
The Cyber Incident Reporting for Critical Infrastructure Act introduces new security incident disclosure requirements for critical infrastructure entities in the United States. Under this act, critical infrastructure operators are mandated to report cybersecurity incidents to the Cybersecurity and Infrastructure Security Agency (CISA) within specific timeframes. Security incident disclosure is required typically within 72 hours after the entity reasonably believes a covered incident has occurred, and 24 hours after making a ransomware payment.
The act aims to enhance the nation's cybersecurity resilience by ensuring timely and coordinated responses to cyber threats targeting critical infrastructure sectors such as energy, transportation, healthcare, and financial services. It requires organizations to report significant cyber incidents that could impact national security, public safety, or economic stability.
Critical infrastructure entities must provide detailed information about the nature of the incident, the affected systems, potential impact, and mitigation measures taken. By promoting information sharing and collaboration between government agencies and private sector organizations, the act seeks to improve incident response capabilities, threat intelligence sharing, and overall cybersecurity readiness across critical infrastructure sectors.
Compliance with the Cyber Incident Reporting for Critical Infrastructure Act is essential for protecting vital national assets, maintaining national security, public safety, and economic stability, reducing the impact of cyber attacks, and strengthening the resilience of critical infrastructure against evolving cyber threats. Key sectors covered include but are not limited to:
- Energy: electricity generation, transmission, and distribution systems, as well as oil and gas infrastructure.
- Transportation: Air transportation, rail systems, maritime ports, road networks critical to move goods and people.
- Healthcare and Public health: Hospitals, Healthcare and public health facilities.
- Financial Services: Banks, financial institutions, payment systems, and stock exchanges.
- Water and Wastewater: Infrastructure related to water supply, treatment, distribution, and wastewater management.
- Communications: Telecommunications networks, internet service providers, and broadcasting systems .
- Emergency Services: Emergency response agencies, law enforcement, fire departments, emergency medical services.
Cybersecurity Maturity Model Certification (CMMC) Program 2.0
The Department of Defense (DoD) Cybersecurity Maturity Model Certification (CMMC) Program version 2.0 draft is a comprehensive framework designed to enhance the cybersecurity posture of defense contractors and subcontractors that handle sensitive information for the U.S. government. Building upon the previous version, CMMC 2.0 introduces updated requirements, guidelines, and maturity levels to strengthen the cybersecurity practices of DoD contractors.
Effective 05/30/2024: DFARS 252.204-7012 introduces a Cyber incident reporting requirement "to Conduct a review for evidence of compromise of covered defense information, including, but not limited to, identifying compromised computers, servers, specific data, and user accounts. This review shall also include analyzing covered contractor information system(s) that were part of the cyber incident" and Rapidly report cyber incidents!
CMMC 2.0 emphasizes a risk-based approach to cybersecurity, focusing on safeguarding Controlled Unclassified Information (CUI) and other sensitive data across the defense industrial base. The program categorizes organizations into different maturity levels, ranging from basic cyber hygiene practices to advanced cybersecurity capabilities, based on their adherence to specific security controls and practices.Key features of CMMC 2.0 include enhanced guidance on security practices, streamlined assessment processes, and improved alignment with industry standards and best practices. The program aims to standardize cybersecurity requirements, reduce cyber risks, and enhance the overall security posture of defense contractors to better protect sensitive information and support national security objectives. Compliance with CMMC 2.0 is essential for organizations seeking to participate in DoD contracts and contribute to the defense supply chain securely and effectively.
New York Department of Financial Services (DFS) cybersecurity regulations, 23 NYCRR 500
The New York Department of Financial Services (DFS) cybersecurity regulations, also known as 23 NYCRR 500, establish comprehensive cybersecurity requirements for financial institutions operating in New York State. These regulations aim to enhance the cybersecurity posture of regulated entities, protect sensitive data, and safeguard the financial services industry from cyber threats.
Key components of the DFS cybersecurity regulations include requirements for conducting risk assessments, implementing cybersecurity programs, maintaining data encryption, establishing incident response plans, and ensuring third-party vendor oversight. Regulated entities are expected to adopt robust cybersecurity measures, such as multi-factor authentication, access controls, regular security training, and continuous monitoring of systems and networks.
The DFS regulations also mandate the reporting of cybersecurity incidents to DFS within 72 hours of discovery and require annual certifications of compliance from senior management. Non-compliance with the regulations can result in penalties and sanctions. By enforcing these regulations, DFS aims to strengthen the resilience of financial institutions against cyber attacks, protect consumer data, and uphold the integrity of the financial services sector in New York State.
Zero Trust Solutions
Our solutions focus on enhancing cybersecurity measures to safeguard your critical infrastructure from cyber threats; creating a more resilient and secure cyber ecosystem by implementing a Zero Trust approach, emphasizing the principle of "never trust, always verify". This shift from traditional perimeter-based security models towards a model where no entity, whether inside or outside the network, is inherently trusted. By adopting a Zero Trust framework, we minimize the risk of unauthorized access and lateral movement within networks, enhancing your security posture.

We tailor security measures to address specific vulnerabilities and threats you face. We customize security solutions based on the unique requirements and characteristics of each system, ensuring a more effective and targeted defense. We prioritize your highest risks first, using Cyber Threat Intelligence datasets about the most relevant current cyber attacks, and measure control effectiveness using the MITRE ATT&CK framework. By leveraging cutting-edge advancements in areas such as artificial intelligence, graph machine learning, cryptography we deliver robust and adaptive security solutions capable of defending against evolving cyber threats. Key layers of our Zero Trust Solutions include:
- User: Continuously authenticate, monitor usage, govern access, privileges, protect with MFA, breakglass. Read more
- Device: Monitor health and status of all devices to inform risk decisions. Real time inspection, patching. Read more
- Applications & Workload: From applications, hypervisors, containers, virtual machines to software supply chain, with fine grained visibility down to software library version and process execution. Read more
- Data: transparency, visibility, data classification, end-to-end encryption, access monitoring tagging. Read more
- Network: Segment, isolate, control (physical and logical) with dynamic, granular policy access controls. Read more
- Automation & Orchestration: Automated security response based on defined processes & security policies enabled by artificial intelligence (AI) (e.g., blocking actions or forcing remediation based on intelligent decisions). Read more
- Visibility & Analytics: Analyze events, activities, and behaviors to derive context and apply AI machine learning to achieve improved detection and reaction times across all metrics, and enables real-time decisions. Read more
Ransomware Defense
Attacked by Ransomware?
Our three step system disrupts Ransomware attacks in progress on your network!!!
Proactive Threat hunting.
Find lurking hackers.
Detect system compromise
Expel unwanted guests.
Identify gaps vs metrics.
Align with Zero Trust.
Enhance security posture.
Ensure detection success.
Real-time alerts with AI.
Rapid Response Team.
Stay ahead of risks.
Secure your digital assets.
Contact us TODAY for a FREE consultation.
Identity Analytics
June 2024 165+ clients affected
Hackers sold stolen data online
Legitimate credentials used
Victims did not have MFA
LYV filed form 8-K 20 May 2024
Machine Identity Management
Managing machine identities, particularly in the context of APIs and cloud services, is essential for ensuring secure and trusted interactions between machines, applications, and services in modern digital environments. Effective management of machine identities plays a critical role in establishing secure communication channels, authenticating entities, and protecting sensitive data. In API management, machine identities, such as API keys, tokens, and certificates, are used to authenticate and authorize access to APIs, ensuring that only authorized entities can interact with the API endpoints.
Proper management of API keys and tokens involves secure generation, distribution, rotation, and revocation to prevent unauthorized access and protect against API abuse or misuse. Managing machine identities is crucial for securing cloud services, virtual machines, containers, and serverless applications. Machine identities, such as SSL/TLS certificates and cryptographic keys, are used to establish secure connections, encrypt data in transit, and authenticate cloud resources to prevent unauthorized access.
Our solutions protect sensitive data, and ensure the integrity and confidentiality of machine-to-machine communications and includes:
- Secure generation, storage: API keys, tokens, certificates.
- Regular rotation & renewal of identities to mitigate risk.
- Monitoring and auditing machine identity usage to detect anomalies and unauthorized access.
- Implementing strong authentication mechanisms, like mutual TLS, to verify the identity of machines and services.
- Integrating MIM solutions with API gateways, cloud platforms, (IAM) systems central control and visibility.
Identity & Access Management
Our Identity & Access Management (IAM) solutions encompass various aspects such as authorization, managing user identities, controlling access to resources, and ensuring secure authentication mechanisms, fine-grained permissions, roles, and privileged user management to enforce access controls and limit exposure to sensitive data and systems. Authorization mechanisms define what actions users can perform and what resources they can access based on their roles and permissions. Fine-grained permissions allow organizations to granularly control access to specific resources, reducing the risk of unauthorized access. Role-based access control (RBAC) assigns permissions based on predefined roles, streamlining access management and ensuring least privilege principles are enforced.
Identity Based Attack Paths
By leveraging graph theory and data visualization techniques, BloodHound maps out the relationships between users, computers, and Active Directory objects to uncover potential security vulnerabilities and privilege escalation paths that attackers could exploit within an organization's network, to deploy ransomware, malware phishing and commit other cybercrime..
Collecting and analyzing data on user permissions, group memberships, and trust relationships to generate a visual representation of your attack surface, allowing identification of high-risk paths that could lead to unauthorized access, lateral movement, or domain dominance by malicious actors. By simulating various attack scenarios and identifying critical paths that attackers could take to compromise sensitive assets, BloodHound enables organizations to proactively strengthen their defenses, remediate security gaps, and enhance their overall cybersecurity posture. The tool provides valuable insights into potential security risks, helps prioritize remediation efforts, and empowers security teams to preemptively mitigate threats before they can be exploited.Privileged User Management
Privileged user management involves monitoring and controlling access for users with elevated privileges to critical systems and data. Implementing strict controls, segregation of duties, and privileged access management (PAM) solutions helps mitigate the risk of insider threats and unauthorized access.
Multifactor Authentication
Multi-factor authentication (MFA) enhances security by requiring users to provide multiple forms of verification before accessing systems or data. Break glass accounts, also known as emergency access accounts, provide a secure mechanism for authorized users to access critical systems in emergency situations.
User Behavior Analytics
User behavior analytics (UBA) and user and entity behavior analytics (UEBA) solutions analyze user activities and behaviors to detect anomalies, suspicious patterns, and potential security incidents. By establishing baselines for normal user and device behavior, organizations can identify deviations and proactively respond to security threats.
Application account management and monitoring involve securing application accounts, managing API access, and monitoring application activities to prevent unauthorized access and data breaches. Rule-based dynamic access control allows organizations to dynamically adjust access permissions based on contextual factors such as user location, device type, and time of access.
By implementing robust IAM solutions and leveraging advanced security technologies such as MFA, UBA, and dynamic access controls, organizations can strengthen their cybersecurity defenses, protect sensitive data, and mitigate the risks associated with unauthorized access and insider threats.
Cyber Attack Surface Management

Our comprehensive Attack Surface Management (ASM) solutions are designed to help organizations identify, assess, and manage their attack surface to enhance cybersecurity posture, reducing potential incidents like ransomware, malware phishing and other cybercrime.
Our ASM solutions offers a range of capabilities to proactively monitor and protect against potential security threats, including:
- Continuous asset discovery identifies all assets on your network, including devices, applications, and services. Maintaining an up-to-date inventory of assets, is vital to understand your attack surface and potential vulnerabilities.
- Vulnerability assessment and prioritization scans assets for known vulnerabilities and assigning risk scores based on severity, exploitability, and potential impact. This allows organizations to prioritize remediation efforts and focus on addressing the most critical security issues first.
- Threat intelligence integration provides real-time information on emerging threats and vulnerabilities; leveraging threat intelligence feeds, organizations can take proactive measures to protect their assets from active threats.
- Remediation tracking and reporting capabilities, allow organizations to track the progress of security remediation efforts and generate reports to demonstrate compliance with security standards and regulations.
Overall, our Attack Surface Management solutions provide organizations with the tools and insights needed to effectively manage their attack surface, reduce security risks, and strengthen their overall cybersecurity posture. ASM can help organizations reduce the risk of cyberattacks, protect critical assets, comply with security regulations, reduce key cyber business risks like malware, phishing and ransomware and enhance their overall security posture.
Software Supply Chain Security

The SolarWinds cyberattack, was a sophisticated supply chain attack discovered in late 2020, highlighted the critical importance of software supply chain security and the need for robust mitigation solutions to prevent similar incidents in the future. The attack involved the compromise of SolarWinds' Orion platform, to distribute malicious updates to thousands of organizations, including government agencies and major corporations.
Our solutions address key supply chains risks including:- Dormant backdoors: To evade detection by supply chain security systems, cybercriminals often implant backdoors during a malware attack and leave them for future use. Security teams are distracted by the attack and do not notice the backdoor, which is exploited at a future date.
- Application code: With applications increasingly being created using many third-party components, developers rarely have complete visibility into all of the code. Attackers routinely exploit vulnerabilities buried deep in an application to compromise security and gain unauthorized access to systems and networks.
- Third party visibility: Without proper controls, organizations are unable to see how third parties manage their IT resources. We enable comprehensive visibility by monitoring third party activity.
- Overprovisioning of third-party access rights: Granting excessive access rights to third parties, is a common weakness that can be addressed via third party audits, monitoring of access, and frequent premission review.

Software Supply Chain Analytics
Our robust solutions for securing the software supply chain provide comprehensive visibility and threat detection capabilities. By leveraging advanced machine learning and behavioral analytics, we enable organizations to monitor and protect their software supply chain from potential security risks and vulnerabilities. We enable real-time monitoring of software artifacts, dependencies, configurations, allowing for early detection of anomalies and suspicious activities that could indicate a security breach or compromise.
We enable organizations to gain insights into their software supply chain's security posture, identify vulnerabilities, and proactively mitigate risks to ensure the integrity and security of their software assets. By continuously monitoring the software supply chain for deviations from normal behavior and enforcing security best practices, we help organizations maintain a secure and resilient software development and deployment process. Through automated threat detection and response capabilities, we strengthen organizations software supply chain security and protect against emerging cyber threats, cybercrime, malware and ransomware.
Monitor Sensitive Data

Our comprehensive data protection and compliance solutions are designed to safeguard sensitive data across hybrid cloud, databases, file systems, email services, messaging platforms, including Microsoft Outlook, Microsoft Teams, Slack, Gmail, etc. and big data platforms. We offer a range of capabilities, including automated data discovery, classification, monitoring, encryption, and access control, to help organizations secure their critical data assets and comply with regulatory requirements, such as GDPR and CCPA.
Our solutions encompass the following elements:- Data Discovery: Our data discovery software enables organizations to identify and classify sensitive data across their IT infrastructure, helping them understand where data resides and who has access to it.
- Data access and activity monitoring: provides real-time visibility into data usage, alerts on suspicious behavior, and help organizations detect and respond to potential security threats promptly. We enable businesses to gain valuable insights into their data assets, enabling informed decision-making and enhancing data security.
- Data governance: via a centralized hub, fostering collaboration among data stakeholders and facilitating data lineage tracking for improved data quality and trust. Providing a holistic view of data across the organization, empowers businesses to harness the full potential of their data assets while maintaining data privacy and regulatory compliance.
- Post Quantum Cryptography: We also offer next generation quantum resistant Data encryption capabilities to protect data at rest and in transit, ensuring that sensitive information remains secure and confidential.
- User Monitoring: Access control features allow organizations to enforce granular access policies, restrict unauthorized access, assess user rights levels, monitor application account usage, and monitor privileged account activity.
- Integration: with security information and event management (SIEM) systems, ticket management systems to monitor change control approval, and external incident managemt systems, to provide centralized monitoring, reporting, and compliance management. This integration enables organizations to streamline security operations, automate compliance reporting, and demonstrate adherence to data protection regulations such as GDPR, HIPAA, and PCI DSS.
- Data Loss Prevention: (DLP) capabilities, include prevention of unauthorized disclosure or leakage of sensitive data. DLP features focus on identifying, monitoring, and protecting sensitive data to prevent its loss or exposure to unauthorized parties. Core capabilities include automated discovery and classification of sensitive data, real-time monitoring of data usage and movement, policy enforcement to prevent data breaches, and incident response mechanisms to address security incidents promptly.
Data Threat Analytics

Our comprehensive Data Threat Analytics solutions are designed to help organizations enhance their cybersecurity posture, strengthen incident response capabilities, and protect critical data assets from evolving cyber threats. The solution empowers security teams to proactively identify and mitigate security risks, improve compliance, and safeguard sensitive information in today's dynamic threat landscape. By leveraging advanced analytics, machine learning, and automation capabilities, our Data Threat Analytics provides real-time visibility into potential security incidents, anomalous activities, and unauthorized access attempts.
Key features include:- Behavioral Analytics: Analyzes user and data access patterns, network traffic, and system behaviors to identify deviations from normal activities indicating security threats or insider risks.
- Threat Detection: By correlating security events, logs, and alerts from various sources, Data Threat Analytics can detect indicators of compromise, malware infections, and suspicious activities that may pose a risk to the organization.
- Incident Response: Automated incident response capabilities, enabling security teams to quickly investigate security alerts, contain threats, and remediate security incidents to minimize impact, prevent data loss, and contain attacks.
- Data Protection: Data Threat Analytics integrates with other data protection platforms to provide a holistic approach to cybersecurity, combining threat detection and response with data protection, and ransomware protection.
- Compliance Monitoring: Meet regulatory compliance requirements by monitoring data access, encryption, and privacy controls to ensure data protection and adherence to industry standards.
- Reporting and Visualization: Data Threat Analytics offers customizable dashboards, reports, and visualizations to provide security teams with actionable insights, trends, and metrics related to security incidents and threat intelligence.
Early Warning System

Our state-of-the-art Security Operations Centre (SOC) operates 24/7 to safeguard your digital assets. Our dedicated team of cybersecurity experts works tirelessly around the clock to monitor, detect, and respond to potential threats in real-time, ensuring the highest level of protection for your organization.
We seamlessly integrate advanced technologies and cutting-edge tools, to provide proactive threat intelligence, continuous security monitoring and incident response. Our team of certified professionals is have the expertise to analyze security events, investigate incidents, and implement rapid remediation strategies to mitigate risks effectively. With our SOC's robust capabilities, you can trust that your critical systems and data are under constant surveillance, allowing you to focus on your core business activities without worrying about cybersecurity threats. Our sophisticated analytics capabilities provide unparalleled visibility into your security posture, enabling swift and decisive actions to defend against evolving cyber threats and ensure the resilience of your organization's digital infrastructure.
Cyber Incident Response Retainer Service, is a proactive shield against potential cyber catastrophes.
Gain peace of mind knowing that a team of seasoned experts is on standby, ready to spring into action at a moment's notice. Our tailored retainer ensures rapid response, containment, and recovery in the event of a breach, minimizing downtime and reputational damage. Stay ahead of cyber adversaries with our 24/7 support, threat intelligence, and post-incident analysis.
- Ransomware Early Warning Monitoring System
- Cyber Incident Response retainer service
- 24x7 Security Operations Center
- Level 3 SOC support & optimization services
Contact Us

347-474-0313
Mailing Address: 224 W 35th St., Swt 500.203, New York, NY 10001
Resources
Twitter or LinkedIn
Ransomware Advisories
Cybersecurity Basics
- Cybersecurity 101: A Beginner's Guide
- Top 10 Tips for Online Safety
- NSA and CISA Top Ten Cybersecurity Misconfigurations
- SMALL BUSINESS GUIDE TO CYBERSECURITY
Ransomware Protection
- How to Protect Your Business from Ransomware Attacks
- CIS Ransomware Prevention Checklist
- Recovering from a Ransomware Attack: Step-by-Step Guide
Data Security
- Data Encryption Best Practices
- Post Quantum Encryption
- Securing Sensitive Information: A Guide for Small Businesses
- Single Sign-On (SSO) for Small and Medium-Sized Businesses
Phishing & Malware Tools
- Top Antivirus Software Guide
- Firewall Solutions for Small Businesses
- Password Managers: Why You Need One
Incident Response
- CISA Creating an Incident Response Plan
- Incident Response Team Roles and Responsibilities
- NIST SP 800-61 Rev. 2 Computer Security Incident Handling Guide
Additional Resources
News: TOP STORIES
| CDK Global cyberattack impacts thousands of US car dealerships |
|---|
| Car dealership software-as-a-service provider CDK Global was hit by a massive cyberattack, causing the company to shut down its systems and leaving clients unable to operate their business normally. CDK Global provides clients in the auto industry a SaaS platform that handles all aspects of a car dealership's operation, including CRM, financing, payroll, support and service, inventory, and back office operations. The company is used by over 15,000 car dealerships in North America and has thousands of employees throughout the country. full story |
| Change Healthcare lists the medical data stolen in ransomware attack |
The data breach notifications are for a February ransomware attack on UnitedHealth subsidiary Change Healthcare when attackers stole 6 TB of data from the company.
The attack led to widespread outages in the US healthcare system, preventing doctors and pharmacies from filing claims. The disruption was particularly noticeable in pharmacies, which could not process any insurance claims or accept discount prescription cards, causing some patients to pay full price to receive medications.
The BlackCat (aka ALPHV) ransomware gang conducted the attack, using stolen credentials to log into the company's Citrix remote access service, which did not have multi-factor authentication enabled.
UnitedHealth admitted to paying a ransom demand, allegedly $22 million, to the ransomware gang, which was supposed to be split with an affiliate who conducted the attack. However, the BlackCat operation instead shut down, stealing the entire payment for themselves. full story
 Alleged ALPHV affiliate claims they got scammed of the alleged Optum ransom of $22 million |
| Ivanti RCE flaw may impact 16,000 exposed VPN gateways EMERGENCY DIRECTIVE: ED 24-01: disconnect all instances of Ivanti Connect Secure |
|
CISA Advisory Approximately 16,500 Ivanti Connect Secure and Poly Secure gateways exposed on the internet are likely vulnerable to a remote code execution (RCE) flaw the vendor addressed earlier this week. The flaw is tracked as CVE-2024-21894 and is a high-severity heap overflow in the IPSec component of Ivanti Connect Secure 9.x and 22.x, potentially allowing unauthenticated users to cause denial of service (DoS) or achieve RCE by sending specially crafted requests. Upon disclosure, on April 3, 2024, the internet search engine Shodan showed 29,000 internet-exposed instances, while threat monitoring service Shadowserver reported seeing roughly 18,000. At the time, Ivanti stated that it had seen no signs of active exploitation in any of its customers but urged system administrators to apply the updates as soon as possible. Two days later, Shadowserver added CVE-2024-21894 into its scanning capabilities, reporting that about 16,500 instances are vulnerable to the RCE flaw. |
| The MOVEit Transfer data theft attacks |
|
CISA Advisory Reports of widespread data-theft attacks exploiting a zero-day vulnerability in the MOVEit Transfer secure file transfer platform. MOVEit Transfer is a managed file transfer (MFT) solution developed by Ipswitch, a subsidiary of US-based Progress Software Corporation, that allows the enterprise to securely transfer files between business partners and customers using SFTP, SCP, and HTTP-based uploads. While the vulnerability was patched in May 2023, the threat actors had already utilized it as a zero-day to breach MOVEit Transfer servers and download the stored data. The attacks were soon claimed by the Clop ransomware gang, who previously launched similar attacks through zero-day vulnerabilities in Accellion FTA and GoAnywhere. According to Emsisoft, 2,706 organizations were breached using this vulnerability, exposing the personal data of over 93 million people. CISA Actions to take today to mitigate cyber threats from CL0P ransomware:
|
MGM Resorts Scattered Spider cyberattack shuts down IT systems after cyberattack |
|
CISA Advisory MGM Resorts International suffered a massive attack that impacted numerous systems, including its main website, online reservations, and in-casino services, like ATMs, slot machines, and credit card machines. The BlackCat ransomware operation claimed the attack, whose affiliates said they encrypted over 100 ESXi hypervisors during the incident. Bloomberg reported that the same group also breached Caesars Entertainment's network, providing a strong hint in a form 8-k SEC filing that they paid the attackers to prevent a leak of customers' stolen data. While the attack was significant, it also brought wide attention to a loose-knit group of hackers known as Scattered Spider. Scattered Spider, also known as 0ktapus, Starfraud, UNC3944, and Muddled Libra, is adept at social engineering and relies on phishing, multi-factor authentication (MFA) bombing (targeted MFA fatigue), and SIM swapping to gain initial network access on large organizations. 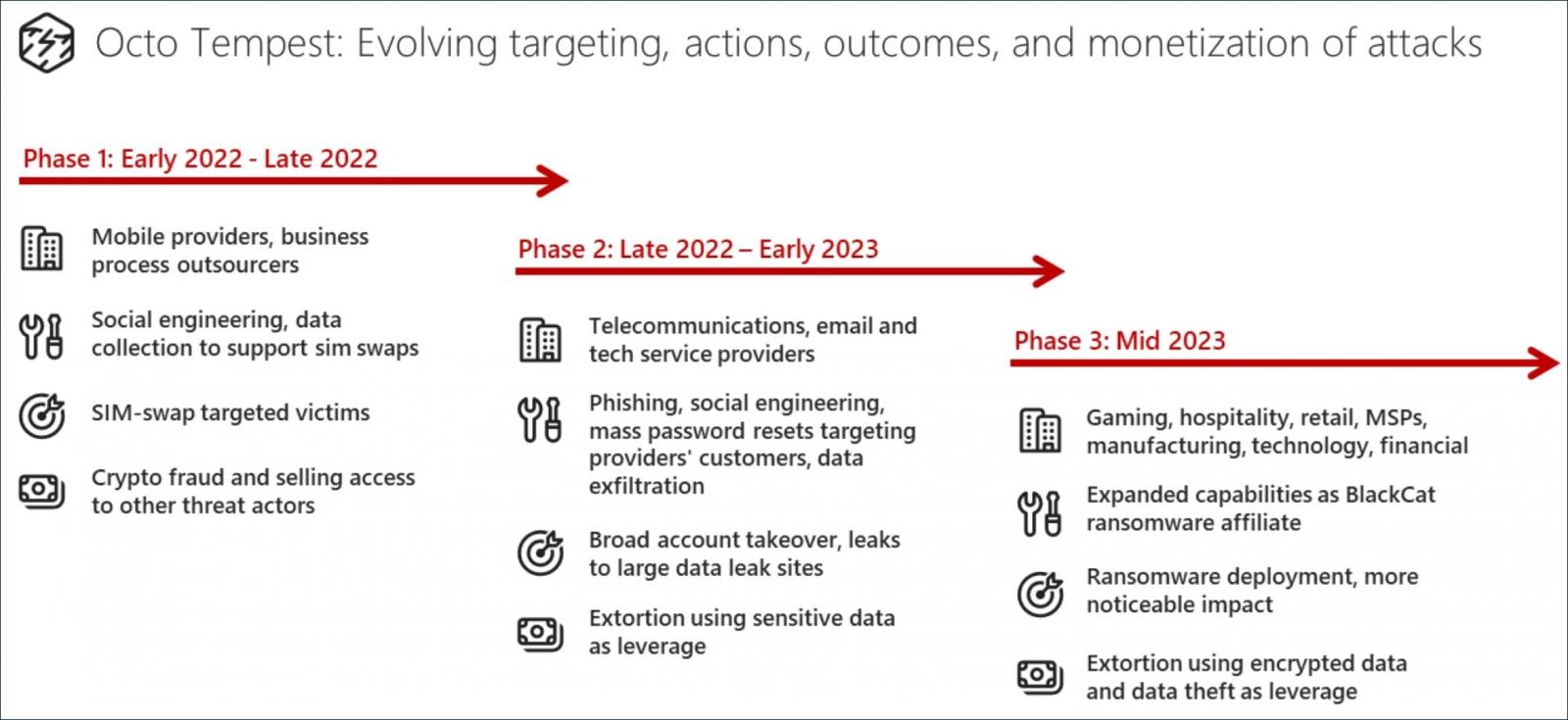 Scattered Spider's evolution (Microsoft guidance) Members of this collective are affiliates of the BlackCat ransomware gang and include young English-speaking members with diverse skill sets who frequent the same hacking forums and Telegram channels. While many believe this is a cohesive gang, the group is a network of individuals, with different threat actors participating in each attack. This fluid structure is what makes it challenging to track them. In November, the FBI released an advisory highlighting the group's tactics, techniques, and procedures (TTPs). Scattered Spider is behind previous attacks on Reddit, MailChimp, Twilio, DoorDash, and Riot Games. full story |
| The 23andMe data breach |
| Genetic testing provider 23andMe suffered credential stuffing attacks that led to a major data breach, exposing the data of 6.9 million users. The company states that the attackers only breached a small number of accounts during the credential-stuffing attacks. However, the threat actors were able to abuse other features to scrape millions of individuals' data. The threat actors attempted to sell the stolen data, but after not receiving buyers, leaked the data for 1 million Ashkenazi Jews and 4,011,607 people living in Great Britain on a hacking forum. In a recent update, 23andMe told BleepingComputer that the breach impacted 6.9 million people — 5.5 million through the DNA Relatives feature and 1.4 million through the Family Tree feature. This breach has led to multiple class action lawsuits against the company for not adequately protecting data. full story |
| Hosting firm says it lost all customer data after ransomware attack |
|
CISA advisory Two Danish hosting providers were forced to shut down after a ransomware attack encrypted the majority of customer data, and data restoration was not successful. "Since we neither can nor wish to meet the financial demands of the criminal hackers for a ransom, CloudNordic's IT team and external experts have been working intensively to assess the damage and determine what could be recovered," reads CloudNordic's statement (machine translated) "Sadly, it has been impossible to recover more data, and the majority of our customers have consequently lost all their data with us." The increasing DDoS attacks and their impact led the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to release advisory about these incidents. full story |
| Anonymous Sudan hacktivists show that DDoS attacks can impact the largest tech firms |
|
A hacktivist group known as Anonymous Sudan took everyone by surprise when their DDoS attacks took down the websites and services of some of the largest tech firms in the world. The group's attacks gained wide media attention when they successfully took down login pages for Microsoft's services, including Outlook, OneDrive, and the Azure portal. Over a week later, Microsoft finally confirmed that DDoS attacks caused these outages. "Beginning in early June 2023, Microsoft identified surges in traffic against some services that temporarily impacted availability," confirmed Microsoft https://msrc.microsoft.com/blog/2023/06/microsoft-response-to-layer-7-distributed-denial-of-service-ddos-attacks/ "Microsoft promptly opened an investigation and subsequently began tracking ongoing DDoS activity by the threat actor that Microsoft tracks as Storm-1359." 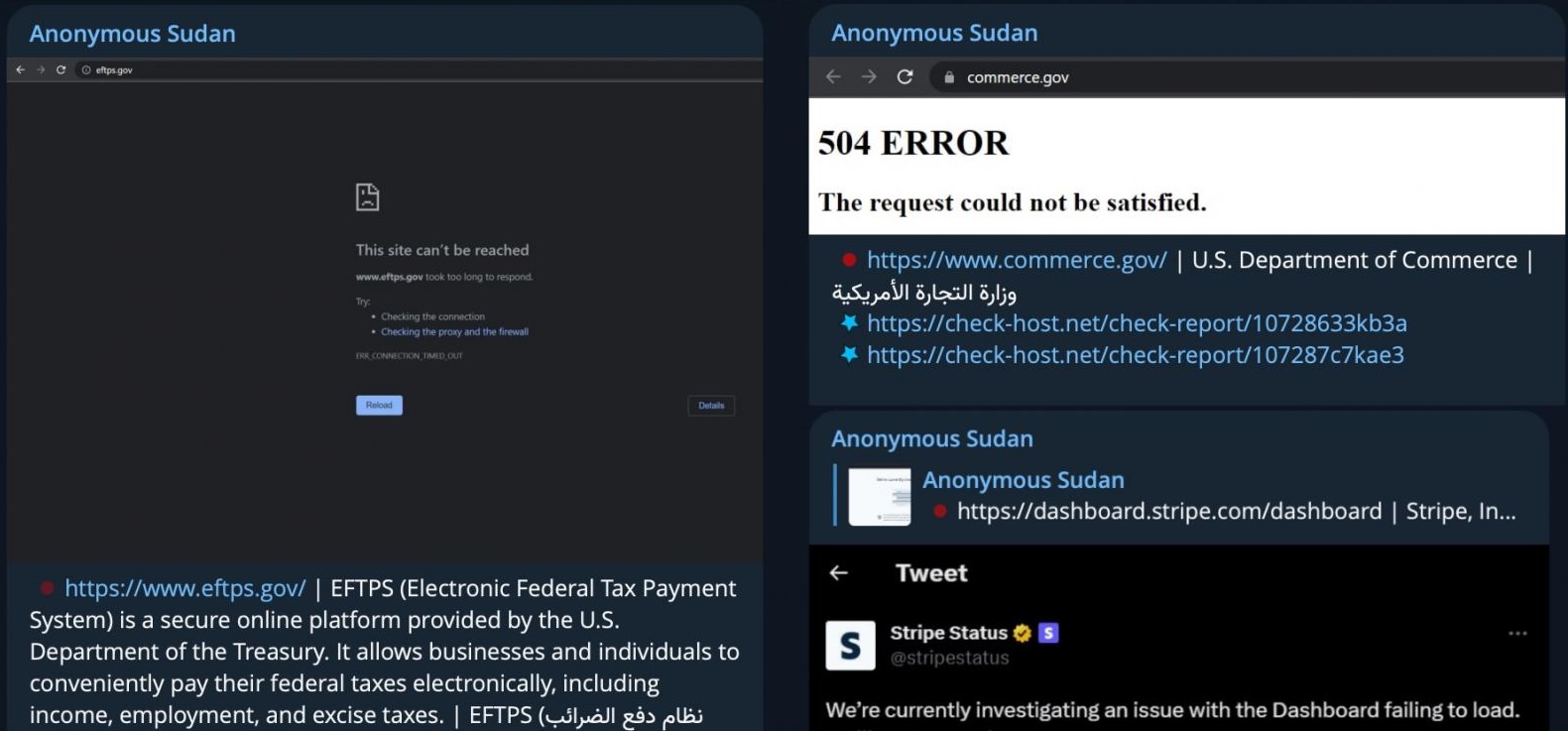 Anonymous Sudan claiming to attack US government websites Anonymous Sudan later targeted numerous other websites, including those for ChatGPT, Cloudflare, and U.S. government services. |
| New acoustic attack steals data from keystrokes with 95% accuracy |
| A team of researchers from British universities trained a deep learning model to steal data from keyboard keystrokes recorded using a microphone with an accuracy of 95%. When Zoom was used for training the sound classification algorithm, the prediction accuracy dropped to 93%, which is still extremely high. To mitigate these attacks, the researchers suggest users may try altering typing styles or using randomized passwords. Other defense measures include using software to reproduce keystroke sounds, play white noise, or software-based keystroke audio filters. full story |
| PayPal accounts breached in large-scale credential stuffing attack |
| PayPal suffered a credential stuffing attack between December 6 and December 8, 2022, allowing attackers to access 34,942 accounts. Credential stuffing is an attack where hackers attempt to access an account by trying out username and password pairs sourced from data leaks on various websites. Hackers had access to account holders' full names, dates of birth, postal addresses, social security numbers, and individual tax identification numbers. full story |
| Dish Network goes offline after likely cyberattack, employees cut off |
|
CISA Advisory Stop Ransomware Black Basta American T.V. giant and satellite broadcast provider DISH Network mysteriously went offline earlier this year, with its websites and mobile apps not working for days. DISH later confirmed that the outage was caused by a ransomware attack, with BleepingComputer first to report that the Black Basta ransomware gang was behind the attack. Employees told BleepingComputer that the ransomware gang compromised the company's Windows domain controllers and encrypted VMware ESXi servers and backups. DISH data breach notifications confirmed that data was stolen in the attack and hinted that a ransom was paid not to release the stolen data. "We are not aware of any misuse of your information, and we have received confirmation that the extracted data has been deleted," read the data breach notification. full story |
| GoDaddy: Hackers stole source code, installed malware in multi-year breach |
| Web hosting giant GoDaddy says it suffered a multi-year breach allowing unknown attackers to steal source code and install malware on its servers. This breach began in 2021 and allowed the threat actors access to the personal information of 1.2 million Managed WordPress customers, including credentials, and also used the access to redirect websites to other domains. No threat actors ever claimed responsibility for this attack. full story |
| Hackers compromise 3CX desktop app in a supply chain attack |
|
CISA Advisory 3CX was breached by the North Korean Lazarus hacking group to push malware through a supply chain attack using the company's Voice Over Internet Protocol (VOIP) desktop client. 3CX is a VoIP IPBX software development company whose 3CX Phone System is used by more than 350,000 companies worldwide and has over 12 million daily users. 3CX was breached after an employee installed a trojanized version of Trading Technologies' X_TRADER software, which allowed the threat actors to steal corporate credentials and breach the network. The attackers pushed out a malicious software update that installed a previously unknown information-stealing malware to steal data and credentials stored in Chrome, Edge, Brave, and Firefox user profiles. full story |
| Barracuda says hacked ESG appliances must be replaced immediately |
|
CISA Advisory In May, Barracuda disclosed that some of their Email Security Gateway (ESG) appliances were hacked using a zero-day vulnerability to install malware and steal data. We later learned that the attacks were linked to Chinese threat actors, who used the vulnerability since 2022 to infect ESG devices with new malware named 'Saltwater,' 'Seaspy,' and 'Seaside.' CISA disclosed that Submarine and Whirlpool malware were also used in the attacks to backdoor ESG devices. What stood out from these attacks is that instead of using a software fix for impacted ESG devices, Barracuda warned customers they must replace their Email Security Gateway (ESG) appliances, which was done free of charge. "Impacted ESG appliances must be immediately replaced regardless of patch version level," the company warned at the time. "Barracuda's remediation recommendation at this time is full replacement of the impacted ESG." This unusual request led many to believe that the threat actors compromised the devices at a low level, making it impossible to ensure they were completely clean. Mandiant, who was part of the incident response in these attacks, told BleepingComputer that this was recommended out of caution, as Barracuda could not ensure the complete removal of malware. full story |
| Massive ESXiArgs ransomware attack targets VMware ESXi servers worldwide |
|
CISA Advisory In February 2023, a massive ransomware campaign targeted exposed VMware ESXi servers worldwide, quickly encrypting the virtual machines for thousands of companies. Just hours after the attack, victims began reporting in the BleepingComputer's forum that files with vmxf, .vmx, .vmdk, .vmsd, and .nvram, all files associated with VMware ESXi virtual machines, were encrypted. The ransomware campaign was dubbed ESXiArgs due to an .args file being created for every encrypted file. The VMware ESXi console home page was modified to show a ransom note demanding 2.0781 bitcoins, worth approximately $49,000 at the time. full story |
| The Operation Triangulation iPhone attacks |
In June 2023, researchers from Kaspersky first disclosed a new zero-click iOS attack called "Operation Triangulation" used to install the TriangleDB spyware on iPhones.
Kaspersky discovered the attack on devices within its own network, and Russia's FSB intelligence service accused Apple of providing the NSA with a backdoor. However, the true origins of the attack remain unknown, and there is no proof that the U.S. government is behind the attacks.
The attacks start with the hackers sending a malicious iMessage attachment that, when processed by iOS, automatically triggers a zero-click exploit chain. A zero-click exploit means it does not require interaction from the user to be triggered.
The attacks chained together four zero-day iOS vulnerabilities listed below to install the spyware:
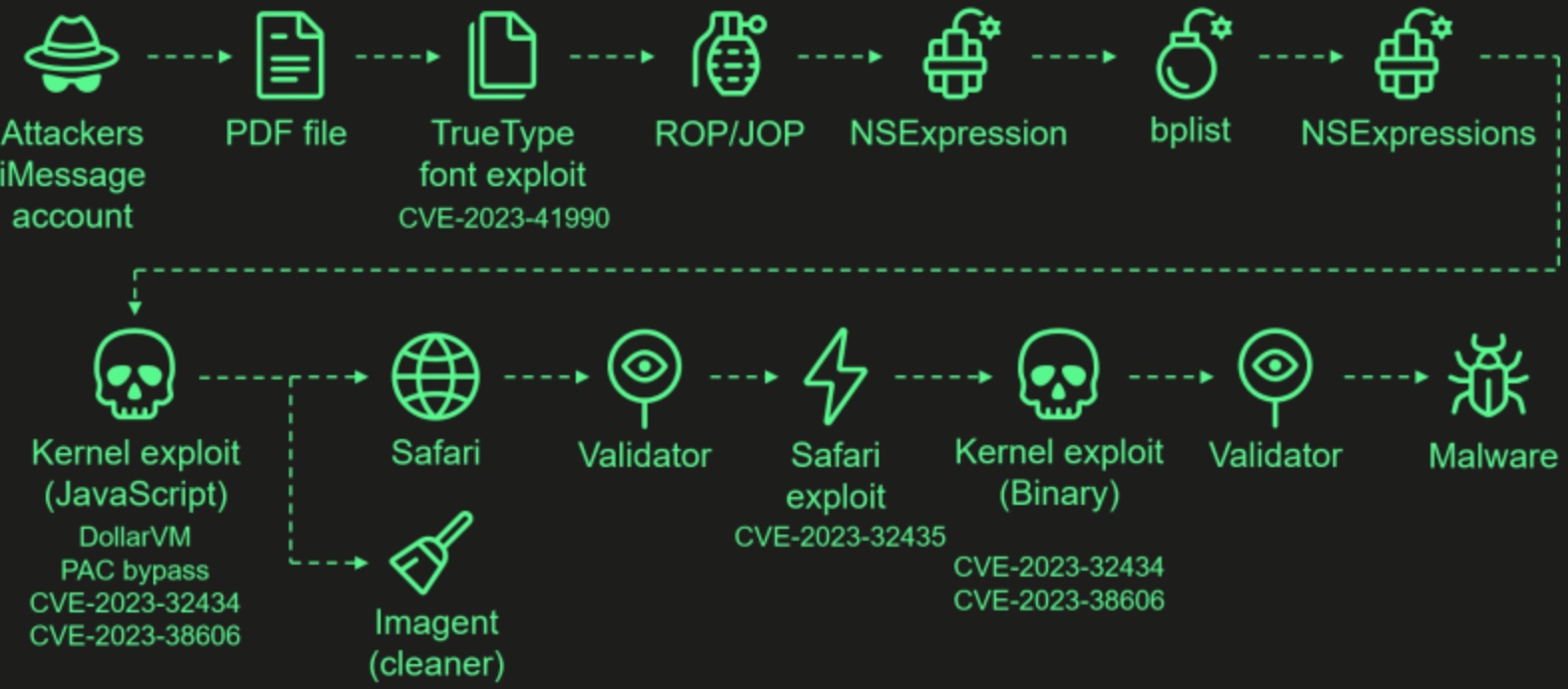 Operation Triangulation attack chain Source: Kaspersky While it's still unknown who is behind the attacks, their sophistication has led cybersecurity researchers to believe that a government-sponsored hacking group is behind them. full story |
Emergency Response
As we prioritize current clients during major ransomware campaigns, ensure immediate assistance with SLA-defined response times by subscribing to our Cyber Incident retainer.
Don't risk delays in critical situations. Secure your spot on our roster TODAY!

UNDER ATTACK?
We are here to help.